Act Now: Tackling and Surviving Microsoft’s Azure AD Graph API Retirement
January 22, 2025 •Matthew Levy
Overview of Azure AD Graph API Retirement
Microsoft Azure Active Directory Graph API or Azure AD Graph API was originally introduced in 2013 to provide programmatic access to Azure AD – The directory part of your Microsoft cloud, now known as Entra ID. In November 2015, Microsoft launched Microsoft Graph API, which offers a more comprehensive and secure approach compared to Azure AD Graph API; this is because it is the API for everything in your Microsoft cloud, not just the directory.
As a result, Microsoft announced the deprecation* of Azure AD Graph API, with plans to retire it completely. The original retirement date was meant to be June 30, 2023, but has been extended to June 30, 2025. Because why? Dates are hard, and organizations (including Microsoft themselves) need more time to get organized.
*Marked as outdated and no longer being actively developed or supported
The retirement of Azure AD Graph API is still happening this year (2025); in fact, Microsoft released their “Sky is falling” Action required blog on December 5, 2024, and another reminder on January 16, 2025. The TLDR is:
-
Microsoft is retiring the Azure AD Graph API, and Microsoft Graph is the replacement.
-
Starting on the 1st of February 2025, applications that still make requests to AAD Graph API will be blocked.
-
New applications created after 31st August 2024 should already have been blocked.
-
You can configure apps to allow extended AAD Graph access until the 30th of June 2025 by modifying authenticationBehaviors attributes using graph (MS Graph, that is)
-
You need to URGENTLY identify applications in your tenant that are dependent on AAD Graph API so you can take action to minimize disruptions and an influx of service tickets.
The purpose of this blog post is to encourage you, Entra ID administrators, to assess your Enterprise Applications and App Registrations for dependencies on the soon-to-be-deprecated API and understand the impact and the actions you need to take.
The role of the Azure AD Graph API
Azure AD Graph API has long been a fundamental tool for interacting programmatically with Azure Active Directory. It enables developers and IT administrators to manage directory resources like users, groups, applications, and Service Principals. REST-based endpoints allowed for automation, integration, and customization of identity management workflows.
However, Azure AD Graph API is now considered legacy technology. Microsoft Graph API is its successor, offering an expansive and unified interface to Microsoft 365 services, including identity and access management. The deprecation of Azure AD Graph API aligns with Microsoft's broader strategy of consolidating its APIs into Microsoft Graph.
Timeline of Deprecation
The key timelines for the retirement of Azure AD Graph are:
- 2019: Initial announcement of the deprecation of Azure AD Graph. Retirement set for June 30, 2023.
- June 30, 2023: End of the three-year notice period for deprecation of Azure AD Graph. Azure AD Graph enters its retirement cycle. I am not sure where the 3-year notice period started, but I guess it was June 2020.
- August 31, 2024: New applications created after this date will not be able to use Azure AD Graph unless they explicitly opt-in for extended access. Existing applications will continue to work.
- February 1, 2025: All new and existing apps must explicitly opt-in for extended access to use Azure AD Graph, including apps created before August 31, 2024.
- June 30, 2025: End of extended access to Azure AD Graph. Azure AD Graph will be fully retired.
Impact on your Entra ID tenant
The deprecation of Azure AD Graph API has significant implications for Service Principals and App Registrations, which are critical components in managing access to resources within Entra ID. Many organizations have custom applications, scripts, and third-party integrations that rely on Azure AD Graph API. This means that starting February 1st, your users may have difficult using applications, or they may stop functioning all-together. We would expect to see a surge in service tickets if organizations don't take action.
When the API is retired on 30th June 2025, legacy integrations will fail if they are not updated to use Microsoft Graph API. Microsoft has provided developers with a migration checklist.
Applications in your Entra ID tenant have already warned you that the particular app uses the legacy API.
 Figure 1: API permissions of an App registration showing the deprecation notice.
Figure 1: API permissions of an App registration showing the deprecation notice.
Microsoft says they will send you a list in email of applications in the last 28 days that have used Azure AD Graph.
Any app using Azure AD Graph will still stop functioning after the retirement.
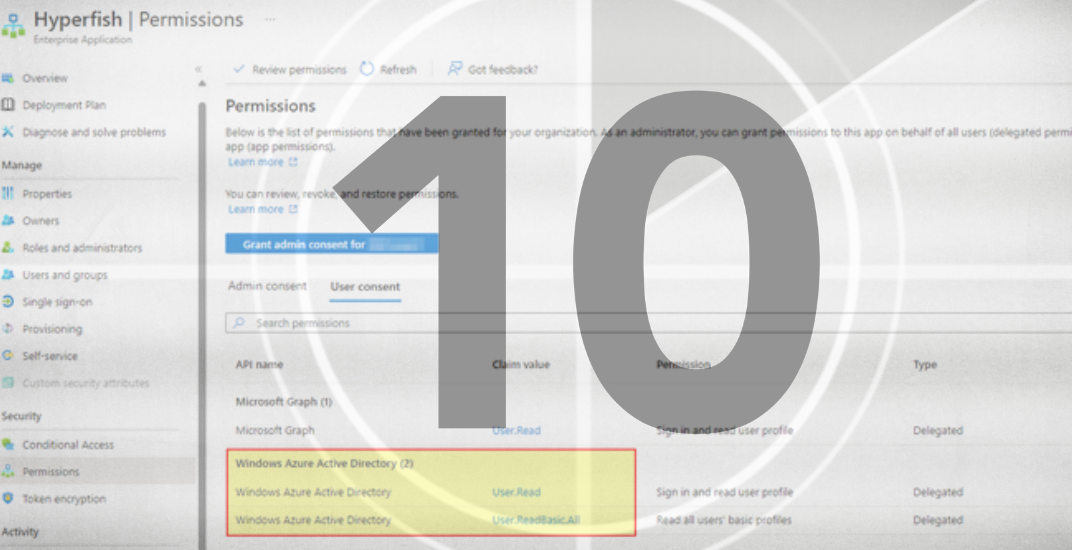
This applies to third-party applications, too. Third-party applications are represented in your tenant by service principals or Enterprise Applications. Third-party applications that use Azure AD Graph need to be updated to newer versions that use MS Graph instead.

Figure 2: Third-party Enterprise App with AAD Graph permissions.
Given that these applications are externally managed, the responsibility for updating them to use the Microsoft Graph API lies with the respective vendors.
“If you have not already, it is now urgent to review the applications on your tenant to see which ones depend on Azure AD Graph API access and mitigate or migrate these before the February 1st cutoff date.”
Challenges in Identifying Dependencies on Azure AD Graph API
Microsoft reckons you can identify and mitigate the use of Azure AD Graph API in “two steps.” Two steps sound simple enough, so let me summarize it for you.
Step One: Identify apps that are using Azure AD Graph in your tenant.
Well, now, does that mean apps that are “actively” using Azure AD Graph or just apps that have Azure AD Graph API permissions?? I can only assume that it means apps actively using the API because Microsoft kindly provided an Entra ID Recommendation to “Migrate Applications from the retiring Azure AD Graph APIs to Microsoft Graph,” which is supposed to list applications that are using the API “currently” (Based on actual usage).
In tenants that I’ve worked with, I know of apps (application registrations) that have Azure AD Graph API permissions, but they don’t show up in the recommendation. In fact, I don’t even get the recommendation at all in one of the tenants I manage, and there are five app registrations with “Windows Azure Active Directory” API permissions.
So, in my mind, I would include those applications in the mitigation plan.
The other types of applications are service principals or Enterprise Applications. Again, Microsoft provides an Entra ID Recommendation to “Migrate Service Principals from the retiring Azure AD Graph APIs to Microsoft Graph,” which is supposed to list service principals or, as Microsoft says, “multi-tenant applications provided by a software vendor” that are used in your tenant and accessing Azure AD Graph API “currently.”
I know I have seriously overused quotation marks here, but I am quoting Microsoft’s blog articles.
 Figure 3: Microsoft Entra Recommendations for Azure AD Graph Retirement.
Figure 3: Microsoft Entra Recommendations for Azure AD Graph Retirement.
This recommendation has been seen in many tenants, but a lot of people have seen only one resource listed as “Microsoft Office” with no further information. See the comments like this one in the TechCommunity blog post:

Never mind, it’s a Microsoft Application anyway, so it’s Microsoft’s problem to solve, right?
“We have ensured that all Microsoft ‘first-party’ applications that are still using Azure AD Graph APIs have the extension through June 2025.”
Microsoft does provide a list of Microsoft Applications here that will not be impacted on the 1st of February.
Step 2: Preparing applications for Azure AD Graph retirement
According to the Entra Recommendations, the two types of applications will need remediation actions. My issue is I have zero applications in the recommendations, but I know about 50 applications in my tenant with Azure AD Graph API permissions. They might not be actively using those API permissions, but they exist.
So, on the one hand, I have application registrations, which need to be updated to use the MS Graph API; on the other hand, I have service principals for vendor-supplied applications.
Just to be sure, I asked my favorite AI tool to generate a KQL query for sign-in logs to list applications accessing Windows Azure Active Directory:
SigninLogs
| where TimeGenerated >= ago(90d)
| where ResourceDisplayName == "Windows Azure Active Directory"
or ResourceId == "00000002-0000-0000-c000-000000000000"
| project TimeGenerated, UserPrincipalName, AppDisplayName, IPAddress, ResourceDisplayName, ResourceId, Status
Okay, so step two essentially says to compile lists of applications that need to be mitigated.
There you have it. There are two simple steps to Azure AD Graph freedom! Right? “Not so fast, Mr. Hicks. You won’t find me doing anything foolish” - Frasier (TV Series)
The inventory part is HARD!
- I’ve tried the Entra recommendations – Pfft, a joke!
- I’ve used the Entra Portal to list app registrations that use Azure Active Directory resource – details here. Useful but inconsistent with other methods.
- I couldn’t get the PowerShell script listed on https://github.com/microsoft/AzureADGraphApps to work because it uses Azure AD Graph – DUH!
- I’ve used the PowerShell script provided by Microsoft to query the recommendations API - not very useful either, and
- I’ve manually gone through hundreds of Enterprise Applications in the Entra Portal to see if they have Azure AD Graph API permissions.
One of the best tools I’ve found to simplify the inventory piece is ENow’s App Governance Accelerator. It provides two reports:
- App Registrations API Permissions
- Enterprise Applications API Permissions
Both reports can be filtered in the tool to list applications with “Windows Azure Active Directory” API access.

Figure 4: App Registrations API Permissions filtered by API.

Figure 5: Enterprise Applications API Permissions filtered by API.
Once I have the filtered report, I export the data to Excel (.xlsx files, not .csv), and I have two lists with which to start my remediation actions.
Steps to mitigate
Once you have the lists, you either must migrate the app (if it’s your own) to MS Graph, configure the app for an extension until June 30, 2025, or get the software vendor (if it’s a non-Microsoft vendor-provided app) to migrate to MS Graph/Apply for an extension.
Microsoft provides instructions for allowing an extension in their documentation - Manage application authenticationBehaviors - Microsoft Graph | Microsoft Learn
You can only modify the authenticationBehaviors parameter of the App Registrations in your tenant with (apps you own or develop). Enterprise Applications that are the service principals for Applications in third-party vendor’s tenants can’t be modified, so you have to contact the vendor and make sure they have either upgraded the app to use MS Graph (in which case you should have the latest version) or the developer has set the authenticationBehaviors "blockAzureADGraphAccess": false.

Figure 6: Graph Explorer PATCH request payload
You could revoke Azure AD Graph permissions for Enterprise Apps in the hope that the app continues to work with MS Graph permissions if there are equivalent permissions on MS Graph. Here’s a comparison list of API permissions.

Figure 7: Revoking AAD permission from Enterprise Application
Act now to avoid application and business disruptions - ENow's Special Trial Offer
It’s crucial and urgent that you assess your Entra ID tenant for applications using the Azure AD Graph API. I talked to the team at ENow, and they’re offering a free upgraded trial of App Governance Accelerator Standard Edition that eligible companies can access until February 1, 2025, to help with the inventory of Enterprise Applications and Application Registrations using Azure AD Graph permissions. Head over to the page above to request your upgraded trial - it's only available for the next 10 days (as of this publishing date).
The AppGov Community also features a Community Forum where you can ask questions and gain clarity from Microsoft MVPs and the ENow team. It can be helpful to compare notes when Microsoft’s recommendations are unclear.
Once inventoried, configure the apps you own that are registered in your tenant for the extension until 30th June 2025, or address the migration if you have sufficient time before the February 1st deadline.
Don’t forget to contact third-party software vendors of Enterprise Applications and get them to migrate to MS Graph, or enable extensions as well!
Good luck, and catch me on the AppGov Forum with your questions!

Written by Matthew Levy
Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.
