Biohacking Entra ID - Identifying Hidden Risks in Entra ID Identities and Applications
April 25, 2025 •Alistair Pugin

This is a supplemental post to our AppGov Score Preventive Maintenance Webinar Series; Season 3, Episode 3: App Governance Biomarkers in Entra ID – Your 100-Day Health Check. The goal of this webinar series is to help you improve your identity & app governance posture in Entra ID.
In this episode, we took viewers through our 100-day plan, which will lead to improvements to overall Cloud Security Posture.
As a precursor to the plan, it was essential for us to establish the rationale and examine various frameworks that have been developed over the years, to support customers, engineers, and consultants alike on their journey.
Identity Management Governance Framework
An Identity Management Governance Framework (IGF) is a structured approach that enables organizations to manage user identities and access rights in a systematic manner. It ensures appropriate access to resources while maintaining compliance with regulatory requirements. Core elements include role management, access certification, and identity lifecycle management, which collectively enhance security and minimize risks.
How the Framework Enhances Your Microsoft Entra ID Environment
We believe that an IGF forms the basis for the metrics you want to establish, allowing you to benchmark the roadmap against a standard framework. This makes sure that you always know what needs to be achieved at a high level.
Implementing an IGF in your Microsoft Entra ID environment offers several benefits:
- Centralized Governance: Provides a unified platform to manage identities, roles, and access across systems, ensuring consistency and reducing mismanagement risks.
- Improved Security: By enforcing least privilege access, conducting regular access reviews, and automating entitlement management, the framework minimizes unauthorized access and potential breaches.
- Compliance Assurance: Built-in audit and reporting tools simplify adherence to regulatory standards, such as GDPR or HIPAA.
- Operational Efficiency: Automating identity lifecycle tasks reduces manual effort, enabling IT teams to focus on strategic objectives.
Key Items for Ensuring Security in Microsoft Entra ID
These key items focus on specific functions that need to exist, and or be implemented in your environment. It serves as a checklist when working through the plan.
To secure your environment effectively, consider the following measures:
- Enable Multi-Factor Authentication (MFA) for all users.
- Use Conditional Access Policies to enforce specific access scenarios.
- Conduct Regular Access Reviews to ensure permissions are up to date.
- Implement Role-Based Access Control (RBAC) to assign roles based on job functions and responsibilities.
- Automate Lifecycle Management for user onboarding and offboarding.
- Encrypt Critical Data using server-side encryption tools.
- Monitor Risky Sign-ins and Users using Entra ID Protection tools.
- Disable Legacy Authentication Protocols to reduce vulnerabilities.
- Enable Privileged Identity Management (PIM) for administrative roles.
100-Day Roadmap for Identity Management Governance
After more than two years of Nic and me discussing monthly how to improve your identity posture in Entra ID, we decided to examine what it would take to implement everything we had been discussing and came up with a plan. For most customers, it's not a greenfield environment; therefore, you have already done some of these things. However, we believe that by following the proverbial “milestones,” it will give you a better chance to cover all the necessary bases you need to quantifiably improve security in your environment.
Days 1–15: Initial Assessment
- Identify existing identity governance gaps.
- Map out all identities, roles, and entitlements in the Entra ID environment.
- Review compliance requirements, such as GDPR and HIPAA.
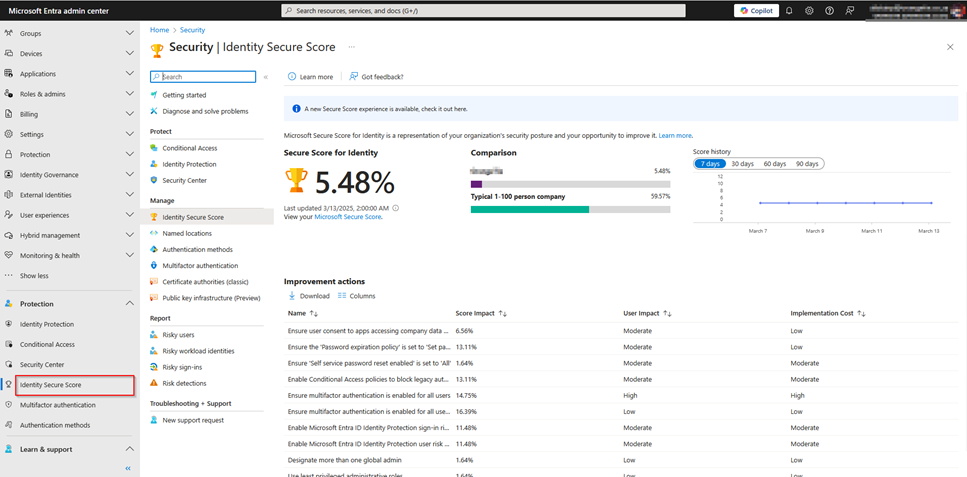
Figure 1. Identity Secure Score
Days 16–30: Policy Definition
- Define access policies based on the principle of least privilege.
- Establish role-based access controls (RBAC) for key job functions.
- Draft a lifecycle management policy for user onboarding and offboarding.
Days 31–45: Implementation of Core Features
- Enable MFA across all accounts.
- Configure Conditional Access Policies.
- Automate entitlement management workflows.
.png?width=973&height=393&name=Multifactor%20Authentication%20with%20Conditional%20Access%20(Microsoft).png)
Figure 2. Multifactor Authentication with Conditional Access (Microsoft)
 Figure 3. Conditional Access Policies
Figure 3. Conditional Access Policies
Days 46–60: Security Enhancements
- Conduct an initial round of automated access reviews.
- Encrypt sensitive data at rest and in transit.
- Implement PIM for managing privileged roles.
 Figure 4. Privileged Identity Management
Figure 4. Privileged Identity Management
Days 61–75: Monitoring and Reporting
- Set up real-time monitoring for risky sign-ins and users.
- Generate compliance reports using Entra ID audit tools.
- Test alerting mechanisms for identity-related risks.
 Figure 5. Sign-in events
Figure 5. Sign-in events
Days 76–90: Optimization
- Fine-tune Conditional Access Policies based on usage analytics.
- Adjust RBAC policies as needed after reviewing user activity logs.
- Automate periodic reviews of inactive accounts.
Days 91–100: Final Review and Documentation
- Conduct a comprehensive audit of the governance framework.
- Document all processes, policies, and configurations implemented.
- Present findings and recommendations to stakeholders.
15-Day Checkpoints
- Day 15: Ensure all identities are mapped; identify gaps in governance policies.
- Day 30: Validate that defined policies align with organizational goals and compliance needs.
- Day 45: Confirm successful implementation of MFA and Conditional Access Policies.
- Day 60: Verify the encryption of critical data and review the results of initial access reviews.
- Day 75: Assess monitoring tools' effectiveness; generate interim compliance reports.
- Day 90: Ensure that optimization steps have addressed the identified issues; prepare for the final review.
Areas to Evaluate in Microsoft Entra ID
Note: Some functions may only exist if you are an E5 customer, but in theory, all you need is one Entra ID P2 Plan license to switch on everything.
- Access Reviews:
- Ensure periodic reviews are automated and effective in identifying discrepancies.
- Entitlement Management:
- Evaluate policies governing resource access requests and approvals.
- Privileged Identity Management (PIM):
- Assess controls over administrative roles to prevent unauthorized access and misuse.
- Lifecycle Workflows:
- Review the automation of user provisioning and deprovisioning processes.
- Conditional Access Policies:
- Analyse their alignment with security requirements and business needs.
- Risk Detection and Mitigation:
- Use Entra ID Protection to actively monitor risky sign-ins and users.
- Data Encryption Practices:
- Validate encryption of sensitive data at rest and in transit.
- Compliance Reporting Tools:
- Test reporting capabilities for regulatory adherence audits.
By following this structured approach, you can establish a robust Identity Management Governance plan that aligns with best practices while leveraging the full capabilities of Microsoft Entra ID under your Microsoft 365 E5 license plan.
But it does not end there.
Want to watch or rewatch Nic and my hot takes? You can view the App Governance Biomarkers webinar replay here.
Stay tuned for Part 2 of this post, where we’ll take you through how to comfortably Assess, Rate, and Remediate Entra ID Applications. Subscribe above to get Part 2 directly in your inbox.

Written by Alistair Pugin
M365 + Security MVP | Blogger | Podcaster | Speaker | Founder, CEO - YModernize
Alistair has worked in various capacities in multiple verticals from retail-manufacturing to government, spanning 50 to 50000 users utilizing all aspects of pure Enterprise Information Management.
Specialties: 20+ years pure IT, 16 years ECM, Livelink, Zylab, SharePoint, FileNet, etc. IT Pro dabbling in Dev, ECM Consultant, Suffering from Technophilia. Technology Architect specializing in Business Productivity Enrichment.
