Microsoft Entra Roles & Application Access
July 11, 2024 •Matthew Levy

In cybersecurity, the principle of least privilege is a cornerstone, advocating for the minimal access required for users to perform their functions. However, in complex IT environments, specific roles necessitate elevated privileges to manage and maintain systems effectively.
As Entra ID administrators, we are well aware of the risks associated with user accounts with the 'keys to the kingdom' when assigned the Global Administrator role or one of the other service administrator roles. However, it's equally important to remember that applications and the users delegated to manage these applications are also at risk, and we must remain vigilant to protect them.
Among the privileged roles found within Microsoft Entra Roles are the Application Administrator role, the Cloud Application Administrator role, and Owner. These Microsoft Entra roles carry significant power and, consequently, significant risks. It's crucial that we manage and oversee these roles with the utmost care and attention.
In one of my previous articles, Identifying OAuth Apps Without Role Assignments in Your Microsoft Tenant, I mentioned that Microsoft Entra Roles can delegate management tasks for Enterprise applications. I simplified admin roles by saying that they dictate which admin types can modify the application object.
Let's examine how these roles can become the focal point for credential theft attacks. Control over them can provide unfettered access to sensitive data and critical systems.
Understanding Microsoft Entra Administrative Roles
Understanding each administrative role's capabilities and potential impact is crucial. Permissions with the PRIVILEGED label help identify permissions that can elevate privilege if not used in the intended and secure manner. What are some of these privileged roles in Microsoft Entra ID that pertain to Enterprise Applications and App Registrations?
If you log into the Entra admin center and go to Identity > Roles and Admins, you can filter the roles by service (in this case, "Applications") and get a filtered list of roles applicable to applications:

Figure 1: Filter roles and admins by service (Applications)
After we filter the view, we have a list of roles, some of which are privileged.

Figure 2: Built-in roles pertaining to Applications in Entra ID
Understanding the Risks and Responsibilities associated with the Application Administrator Role and the Cloud Application Administrator Role
Microsoft Entra Role - Application Administrator Role
The first built-in role in the list is the Application Administrator role. This role typically involves managing user access, configuring application settings, and ensuring the application's availability and security. It is a directory-level role that has inherited access to ALL enterprise apps and app registrations and can only be assigned at the directory level.
This role is privileged and can consent for delegated permissions and application permissions, except for application permissions for tenant-level graph permissions, which require a more privileged role such as Global Administrator.
The Application Administrator Role can add credentials to an application, allowing them to impersonate the application's identity.

Figure 3: Application Administrator can add credentials to an application.
If an application has been granted privileged abilities, a user assigned the Application Administrator role could impersonate it and perform elevated actions, such as creating or updating users or other objects.
Microsoft Entra Role - Application Developer
Next, we have the Application Developer role. Users with the Application Developer role can create and manage application registrations independently. This access includes configuring authentication methods, permissions, and other app settings. The Application Developer role is also a Directory-level role.
They can register web APIs, mobile apps, single-page applications (SPAs), and more.
Application Developers assign permissions to apps. These permissions determine what resources (such as APIs, user data, or other services) an app can access.
They can grant delegated permissions (acting on behalf of users) or application permissions (acting independently). Users with this role can consent to app permissions on their own or others' behalf.
They can manage client secrets associated with app registrations.
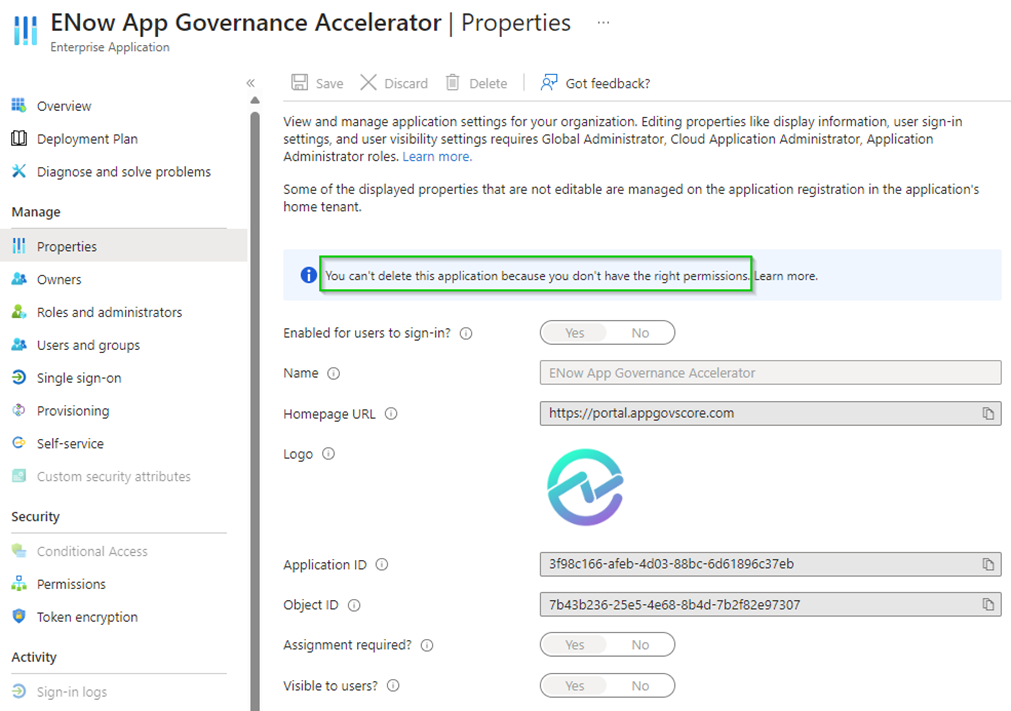
Figure 4: The Application Developer role is restricted from changing some app properties that require elevated permissions.
As you can see from the image above, the Application Developer cannot make some changes to an Enterprise Application because it requires elevated permissions, which this role does not have.
Microsoft Entra Role - Cloud Application Administrator Role
The Cloud Application Administrator role is the same as the Application Administrator role, but with the shift to cloud-based services, this role focuses on overseeing applications hosted in the cloud only. It excludes the ability to manage application proxy. This role enables creating and managing all aspects of enterprise applications and app registrations. This role can be assigned at the Directory-level or an application level, as can be seen in the image below:
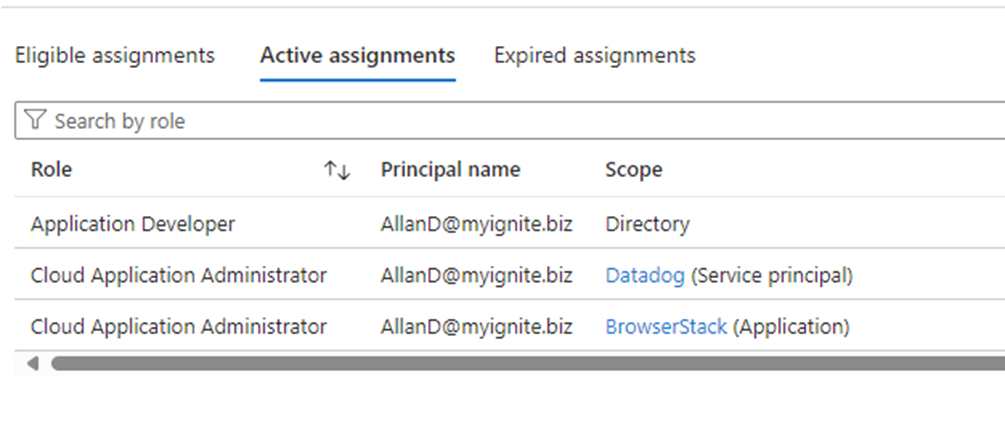
Figure 5: The user is assigned Cloud Application Administrator at the Service Principal and application levels, not the Directory level.
Microsoft Entra Role - Owner
The owner role often holds the highest level of privileges. Owners can make critical decisions about the application's configuration, user roles, and data management policies. The owner role has the same permissions as Application Administrators but is scoped to an individual application.
Users are automatically assigned as owners when they add a new enterprise application. As an owner, they have the ability to manage the tenant-specific configuration of the application, including Single Sign-On (SSO) settings, provisioning, and user assignments. Owners can also add or remove other owners. Unlike those with the Application Administrator role, owners can only manage applications they own.
Currently, only individual users are supported as owners of applications. The assignment of groups as owners is not yet supported.
To list all Enterprise applications that a user is delegated as the owner of in Microsoft Entra ID, follow these steps:
- Log in to the Microsoft Entra admin center as a Global Administrator.
- Navigate to Enterprise Applications.
- Select All Applications.
- Click on Add filter, then use the owner filter to search for apps the specific user owns.
This will display a list of applications associated with the specified owner.

Figure 6: List of Enterprise Apps owned by Allan Deyoung.
These are the built-in roles; as you know, you can create custom roles and assign users those custom roles, too. Be aware that privileged permissions can be assigned to a custom role.

Figure 7: Matt's custom role with privileged permission.
The Dangers of Elevated Privileges
The risks associated with administrator access are multifaceted. Administrators with elevated privileges can make system-wide changes, install software, and access sensitive data. When users are granted more privileges than necessary, while necessary for maintenance and management, this can lead to a condition known as 'overprivileged access,' which is a significant risk for organizations because it opens up several security vulnerabilities.
This excess of privileges can be exploited by malicious actors or even lead to unintended insider threats. The risks associated with overprivileged access are diverse, including unauthorized data access, data manipulation, and the potential for widespread system disruptions.
A recent guide on Microsoft Entra security operations for applications highlights the importance of monitoring application events to prevent breaches. It suggests that applications, while not targeted as often as user accounts, have an attack surface that must be vigilantly guarded. The guide emphasizes the need for continuous monitoring and alerting on application events to prevent malicious applications from gaining unwarranted data access and protect applications from being compromised by bad actors.
Another risk aspect is privilege escalation, where threat actors abuse highly privileged app registrations to move swiftly from lower-level accounts to global administrator accounts. This attack type can be particularly damaging as it allows for rapid and extensive access to an organization's IT environment.
Attackers have exploited highly privileged app registrations to escalate access within an organization's IT environment. By moving from lower-level accounts to global administrator accounts, they gained extensive access to sensitive data and systems.
Anvilogic's threat report discussed the intricate attacks targeting privileged accounts and the tactics, techniques, and procedures used by the threat actors to compromise Okta customers.
Privileged Access Management Best Practices for Microsoft Entra Roles
To mitigate the risks associated with administrative privileges, Entra ID Admins should implement the following best practices:
1. Regular Audits: Conduct frequent reviews of access rights to ensure they align with current job requirements and that any unnecessary privileges are revoked.
Enow's App Governance Accelerator provides reports on application administration privileged users and service principals in your tenant and the application with and without owners. These reports help you review those privileged role assignments and applications that are potentially an avenue for privilege escalation if their owner-designated accounts become compromised. Combine these two reports with the "API Permissions with Privilege Escalation Capability" report. You can get a clear picture of the exposure posture of your tenant to privilege escalation risk.
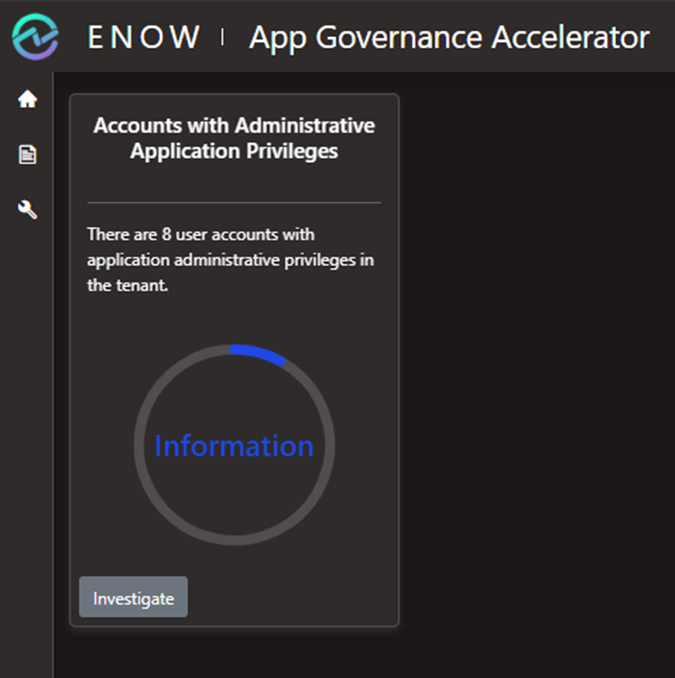
Figure 8: Accounts with Administrative Application Privileges Report in App Governance Accelerator.

Figure 9: Applications without owners report in App Governance Accelerator.
2. Multi-Factor Authentication (MFA): MFA should be required for all administrators to add an extra layer of security against unauthorized access.
3. Least Privilege Principle: Continuously evaluate and adjust privileges to ensure administrators have only the access necessary to perform their duties. Utilize Entra ID's Privileged Identity Management (PIM) for just-in-time access, with approvals, automatic removal, and notification systems.
4. Access Reviews: Regularly audit access to ensure only authorized individuals maintain their permissions and use access reviews to revoke unneeded privileges.
5. Use Cloud native accounts for privileged roles: Don't use on-premises synced accounts for admin role assignments. Best Practices for Microsoft Entra Roles - Microsoft Entra ID states, "If your on-premises account is compromised, it can compromise your Microsoft Entra resources as well."
6. Monitoring and Alerting: Implement real-time monitoring and alert systems to quickly detect and respond to suspicious activities.
Enow's App Governance Accelerator can alert you on suspicious privilege escalation activity:

Figure 10: Alert feature in App Governance Accelerator.
7. Education and Training: Ensure that all administrators know the risks associated with their access and have access to training in security best practices.
Administrator Access to Applications - Final Thoughts
Overprivileged access can pose significant risks to Microsoft Entra Enterprise Apps and your organization's data. The Microsoft Entra roles that grant administrative access carry great responsibility and risk. By understanding these roles and implementing privileged access management best practices, organizations can safeguard their systems against the inherent dangers of elevated privileges. It is a delicate balance between empowering those who maintain our systems and protecting the integrity and security of our digital assets.
Do you know how many accounts have Administrative Application Privileges? The ENow AppGov Score is a free security assessment tool that will quantify your application security and governance state quickly. In addition to providing your AppGov Score, the tool will provide a comprehensive Application Governance Assessment report that includes each test, your result, and why the test matters. Ignorance isn't bliss - it's a breach waiting to happen. It only takes one app, so sign up to get your score and assessment report in just a few minutes - Get Your AppGov Score today!

Written by Matthew Levy
Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.
