Risk Reality – Consequences of Unclear Application Governance in Entra ID
April 16, 2025 •John O’Neill Sr
Welcome to Part 3 of our blog series, Hot Potato – Who Should Own Application Governance in Entra ID. In Part 1 and Part 2 of this series, we...
Read MoreShould ‘Do not allow user consent’ be the new Microsoft recommendation to tackle Malicious OAuth apps?
March 25, 2025 •Sander Berkouwer
Integrating applications, services and systems with Microsoft Entra ID brings organizations many benefits. People who need apps for their...
Read MoreHot Potato – Who Should Own Application Governance in Entra ID? (Part 2)
March 20, 2025 •John O’Neill Sr
In Part 1 of this series, 'Hot Potato - Who Should Own Application Governance in Entra ID,' we introduced the application governance challenge in...
Read MoreLike the title says, Nicolas and I have over the years, taken umbrage in how easy it is to do things in Entra ID.
And because of that, we felt that...
Read MoreHot Potato – Who Should Own Application Governance in Entra ID? (Part 1)
March 6, 2025 •John O’Neill Sr
Applications are the lifeblood of productivity in today's Cloud-first world. From collaboration tools to CRM systems, specialized software powers...
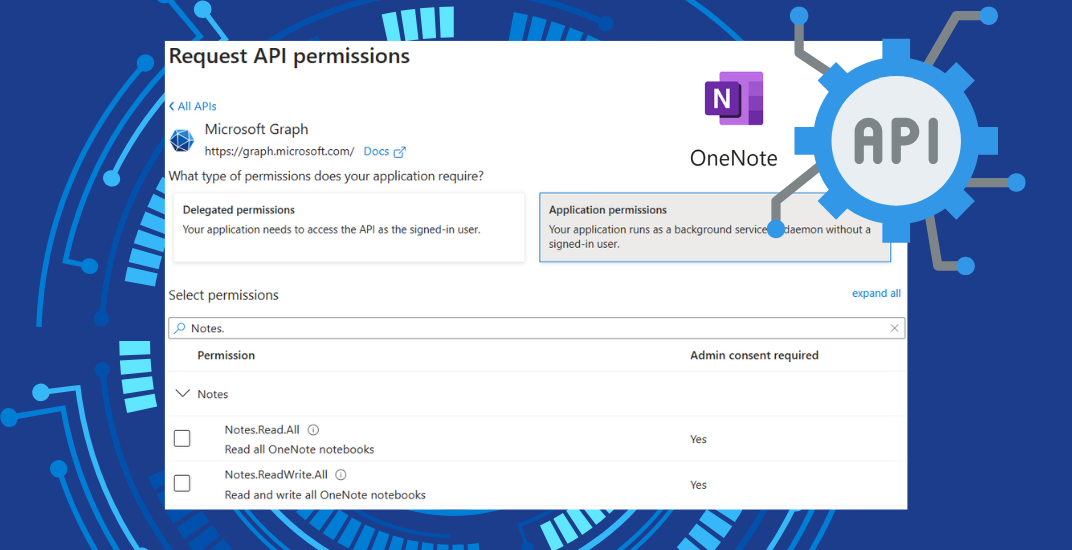
Read MoreUpdate Your OneNote API Permissions Before March 31, 2025, to Prevent Outages
February 27, 2025 •Sander Berkouwer
Microsoft plans to disable OneNote’s app-only permissions to improve security to its advanced note-taking app. When your Entra apps rely on this...
Read More2024 Top AppGov Score Resources for Application Governance & Security
January 2, 2025 •ENow Software
As we start 2025, we wanted to take a moment to highlight some of the greatest AppGov moments of 2024. From blog postswritten by Microsoft MVPs to...
Read MoreEmbracing Zero Trust for Application Security in Entra ID: An Incremental Journey
November 7, 2024 •Nicolas Blank
In our previous webinar on this topic, Zero Trust for Application Security in Entra ID, we made the point that in a cloud landscape, with a massive...
Read MoreConnect to the Microsoft Graph API securely using a Function App and Azure Key Vault
October 24, 2024 •Louis Mastelinck
In a previous blog post, we demonstrated how to authenticate to the Microsoft Graph API using two different methods. The focus was on running a local...
Read More